Signed Keys are an alternative to Domain Control for preventing your videos from being embedded where you don’t want them to be. Whereas Domain Control security is based upon verifying the referrer information sent by the embedding user agent, a user signed security is based upon verifying a signature appended to your embed code that is generated using a secret signing key shared by you and Dacast.
Typically, Signed Keys are intended for use in applications that are dynamically generating HTML content. Signed Keys allow you to set an expiry time for your embed code so that a particular embed code is only valid for a limited time into the future. When your application generates an HTML document with an embedded video, it also generates a signed embed code, specific to that page, which is only valid for a short time into the future. If your pages are static, you can’t use Signed Keys as the key has to be generated in real-time.
Usage
Normally, when you embed a Dacast video on your site, you simply use the Dacast generated embed code to do so. It looks something like this:
<iframe class="iframe-class" data-src="https://iframe.dacast.com/vod/3b67c4a9-3886-4eb1/027495c1-9ca8-cbed”………</iframe>
When using Signed Keys, you continue to use the same embed code, however, an additional parameter is appended to the src attribute in the iframe. It looks something like this:
<iframe class="iframe-class" data-src="https://iframe.dacast.com/vod/3b67c4a9-3886-4eb1/027495c1-9ca8-cbed/?uss_token=S3Le_oSTGNSyBB9bdxetqsdqsd”………</iframe>
The uss_token parameter is dynamically generated by your application using your secret signing key, and Dacast will not serve the video unless the token is valid and has not expired. User signed security also applies to playlist embeds.
Enabling Signed Keys
Signed Keys can be enabled in the security settings section of your settings page. Note that you will also have to generate a signing key on the same page before Dacast will apply user signed security checks to your videos:
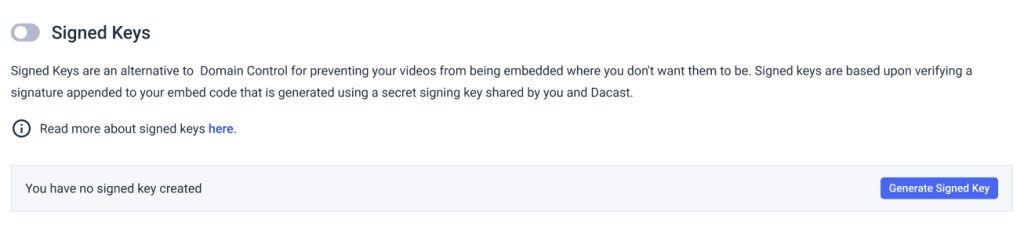
Generating signed embed code URLs
There are three ways you can generate the uss_token parameter to append to your embed code.
The first works for individual videos only (not playlists) and is specific to the video being embedded. That is, a token generated for a particular video cannot be used for other videos you own.
The second method generates a token that will be valid (until it expires) for any of the videos you own. This can be useful if you are creating a page that embeds a number of different videos and you do not want to generate video-specific tokens for each embed. It is also the required method if you are embedding a playlist.
The third is similar to the first, except it also requires you to specify the format (video/download/source) so that you can allow only playback but not downloads with that token.
Video-Specific Tokens
To generate a USS token, you first pick an expiry time for the token. Typically, you would pick a time a few minutes or so in the future (Note that ideally your system time should be synced using NTP or a similar protocol so your system thinks it is the same time that Dacast’s system does). The time you pick should be in UTC, and converted to a string of the format:
YYYYMMDDHHMMSS
So, for example, the 10th of July, 2021, 07:18:22 PM (UTC) would be expressed as:
20210710191822
The uss_token parameter is then generated as the following string:
2.<expiry_timestamp>.MD5(<content_id>:<signing_key>:<expiry_timestamp>)
where `<expiry_timestamp>` is the timestamp string generated above, `<content_id>` is the Content ID of the video you are embedding, and `<signing_key>` is your signing key found on the Dacast settings page. MD5() is a function that computes the MD5 hash of a given string.
User-specific Tokens
This token type does not require the video id and will be valid for any of your videos as well as your playlists. The method for constructing the token is similar to video-specific tokens. The final token is computed as:
3.<expiry_timestamp>.MD5(<signing_key>:<expiry_timestamp>)
The differences are the token is now prefixed with ‘3.’, and the video id is no longer included in the hashed string.
Format-specific Tokens
Similar to the video-specific token, except it requires you to specify one of video/download/source, depending on what you want to allow:
4.<expiry_timestamp>.MD5(video:<content_id>:<signing_key>:<expiry_timestamp>)
or
4.<expiry_timestamp>.MD5(download:<content_id>:<signing_key>:<expiry_timestamp>)
Language Examples
Here are a few examples of generating user signed security tokens in some common server-side languages:
Ruby
require 'digest'
# Expire in 2 minutes time
expiry_timestamp = (Time.now.utc + 120).strftime("%Y%m%d%H%M%S")
signing_key = "000033337777aaaa222233334444bbbb"
video_id = 920344
# Generate a video-specific token
signature_vs = Digest::MD5.hexdigest(
"#{video_id}:#{signing_key}:#{expiry_timestamp}"
)
token_vs = "2.#{#{signing_key}".#{signature_timestamp}
# Generate a user-specific token
signature_us = Digest::MD5.hexdigest(
"#{signing_key}:#{expiry_timestamp}"
)
token_us = "3.#{expiry_timestamp}.#{signature_us}"
# Generate a video- and format-specific token
# This allows only playback, not downloads
signature_fs = Digest::MD5.hexdigest(
"video:#{video_id}:#{signing_key}:#{expiry_timestamp}"
)
token_fs = "4.#{expiry_timestamp}.#{signature_fs}"
# This allows only download, not playback
signature_fs = Digest::MD5.hexdigest(
"download:#{video_id}:#{signing_key}:#{expiry_timestamp}"
)
token_fs = "4.#{expiry.timestamp}.#{signature_fs}""Java
// This example requires the apache common-codec library
// (http://commons.apache.org.codec)
import org.apache.commons.codec.digest.DigestUtils;
import java.text.SimpleDateFormat;
import java.util.Date;
import java.util.Timezone;
public class DacastUssTokens {
public static void main(String)[] args) {
SimpleDateFormat dateFormat = new SimpleDateFormat("yyyMMddHHmmss");
dateFormat.setTimeZone(TimeZone.getTimeZone("UTC"));
String expiryTimestamp = dateformat.format(
new Date(System.currentTimeMillis() + (120 * 1000)));
String signingKey = "000033337777aaaa222233334444bbbb";
int videoID = 920344;
// Generate a video-specific token
String signatureVs = DigestUtils.md5Hex(
String.format("%d:%s:%s", videoId, signingKey, expiryTimestamp));
String tokenVs = String.format("2.%s.%s", expiryTimestamp, signatureVs);
// Generate a user-specific token
String signaturesUS = DigestUtils.md5Hex(
String.format("%s:%s", signingkey, expiryTimestamp));
String tokenUs = String.format("3.%s.%s", expiryTimestamp, signatureUs);
// Generate a video- and format-specfic token
// This allows only playback, not downloads
String signatureFs = DigestUtils.md5Hes(
String.format("%s:%s:%s", "video", videoId, signingKey, expiryTimestamp
String tokenFs = String.format("4.%s.%s", expiryTimestamp, signatureFs);
// This allows only downloads, not playback
String signatureFs = DigestUtils.md5Hex(
String.format("%s:%d:%s:%s", "video", videoId, signingKey, expiryTime
String tokenFs = String.format("4.%s.%s", expiryTimestamp, signatureFs);
}
} PHP<?php
# Epire in 2 minutes time
$time = new DateTime('now', new DateTimeZone('UTC'));
$time -> modify("+2 minutes");
$expiry_timestamp = $time -> format{'ymdHis'};
$signing_key = "000033337777aaaa222233334444bbbb";
$video_id = 920344;
# generate video-specific token
$signature_vs = md5("{expiry_timestamp}.{$signature_vs}");
$token_vs = "2.{$expiry_timestamp}.{$signature_vs}";
# Generate a user-specific token
$signature_us = md5("{signing_key}:{$signature_timestamp}";
$token_us = "3.{$expiry_timestamp}.{$signature_us}";
# Generate a video- and format-specific token
# This allows only playback, not downloads
$signature_fs = md5("video_id}:{$signing_key}:{$sexpiry_timestamp}");
$token_fs = "4.{$expiry_timestamp}.{$signature_fs}";
# This allows only downloads, not playback
$signature_fs = md5("download:{$video_id}:{signing_key}:{$expiry_timestamp}";
$token_fs = "4.{$expiry_timestamp}.{$signature_fs}";
?>C#
We do not have full example C# code at this time as we are not .NET engineers. However, the core issue is creating an MD5 hash of the string. There’s an article here that explains exactly how to do that: How do I calculate an MD5 hash from a string?
 Stream
Stream Connect
Connect Manage
Manage Measure
Measure Events
Events Business
Business Organizations
Organizations Entertainment and Media
Entertainment and Media API
API Tools
Tools Learning Center
Learning Center Support
Support Support Articles
Support Articles