Top Features to Look for in a Secure Video Streaming Platform [2025 Update]
Online video is a powerful medium that is becoming more popular in many industries. It is commonly used by businesses, educational institutions, government agencies, and other professional organizations.
As the online streaming industry grows, so do the threats from hackers and pirates. Unfortunately, there are groups of people with bad intentions that take advantage of broadcasters. This makes secure video streaming more important than ever.
In this article, we are going to discuss the top security features you’ll want to consider when selecting a secure video streaming platform. These features should give you the security you need to deliver both live stream and on-demand video content.
To get started, let’s review what secure streaming is and why modern broadcasters need to consider it.
What is Secure Video Streaming?


Secure video streaming is a form of online video streaming that prioritizes privacy and security. There are several connotations of secure streaming, and there are several ways to approach it.
For some, secure streaming might be as simple as using password protection to keep unwanted viewers off of their stream. For others, secure video streaming might be a bit more complex with state-of-the-art encryptions and more intensive security protocols.
Why Use Secure Video Streaming?
In 2020, the online video streaming industry was valued at $50.1 billion. The industry is expected to grow to a whopping $184.27 billion by 2027.
With this growth potential, secure video streaming is absolutely essential, especially for broadcasters that are using video monetization or are streaming private content. Why? With rising usage comes increased security risks.
In recent years, security firms have registered an increase in piracy, hacking, and other digital attacks. Piracy alone costs the U.S. economy more than $29.2 billion per year. The costs of cybercrime are predicted to be $10.5 trillion in 2025
Aside from the growing threats, secure video streaming comes in handy in situations where broadcasters simply would like to keep their content private.
Artificial Intelligence in Secure Video Platforms
Artificial Intelligence (AI) is transforming secure video platforms, offering smarter ways to protect and manage enterprise video streaming security. By integrating AI, businesses can enhance video content protection with advanced tools like automated threat detection, real-time monitoring, and user behavior analysis. These features identify potential risks and mitigate them before they escalate, ensuring business video content protection at every level.
For corporate video streaming solutions, AI simplifies compliance by ensuring encrypted video streaming for enterprises meets regulatory standards. It also streamlines access control, using facial recognition or behavioral patterns to authenticate users securely.
When it comes to secure live video broadcasting for businesses, AI-powered analytics help monitor streams in real time, flagging unauthorized access or suspicious activities. This ensures businesses can deliver seamless, secure streaming experiences while safeguarding valuable content. By leveraging AI, enterprises can achieve robust video security tailored to their unique needs.
Emerging Technologies for Secure Video Streaming
Emerging technologies are transforming secure video streaming, offering advanced solutions to protect corporate content. AI-driven threat detection is at the forefront, with machine learning analyzing access patterns to identify and block piracy or unauthorized use in real-time. This innovation enhances video DRM for corporate content, making platforms more reliable.
Blockchain technology is also reshaping protected business video streaming services. By creating immutable transaction records, blockchain strengthens digital rights management (DRM), preventing unauthorized duplication of licensed content.
Zero Trust Architecture (ZTA) is gaining momentum in secure corporate webcast platforms, emphasizing continuous user verification and limiting access based on strict controls. This approach aligns well with business video streaming compliance, ensuring security and regulatory adherence.
Lastly, quantum encryption research holds promise for ultra-secure streaming in the future, offering unbreakable encryption methods to further safeguard sensitive corporate videos. These technologies set new standards for secure, compliant streaming solutions.
Comparative Analysis of Secure Video Platforms
Choosing the right video platform for your business requires understanding its security features. Platforms like Dacast, Brightcove, Vimeo, and IBM Video Streaming offer varying enterprise-grade video streaming security features. These include encryption, DRM, tokenization, and AI-driven monitoring, which are critical for enterprise video protection tools.
For example, Dacast excels with dynamic tokenization to prevent unauthorized access, while Brightcove offers robust DRM integration. Vimeo provides simple business video privacy solutions, including password-protected links, but lacks advanced features like biometric authentication, which IBM Video Streaming has started exploring.
The table below compares key cybersecurity for video streaming features:
| Platform | Encryption | DRM | Tokenization | AI Monitoring | Biometric Auth |
| Dacast | AES-256 | Yes | Dynamic | No | No |
| Brightcove | AES-256 | Advanced | Basic | Yes | No |
| Vimeo | AES-128 | Basic | Limited | No | No |
| IBM Video | AES-256 | Advanced | Basic | Yes | Yes |
Benefits of Secure Video Streaming for Businesses in 2024 and Beyond
Secure video streaming offers businesses significant benefits in 2024 and beyond, supporting brand trust, compliance, and operational efficiency. By utilizing professional video streaming platforms with robust security features, businesses can prevent data breaches that could damage their reputation. Encrypted live streaming services and advanced video encryption standards for business ensure sensitive content remains protected, fostering trust with clients and partners.
Compliance with global regulations, such as GDPR in the EU, HIPAA in the US, and China’s PIPL, is simplified when using corporate video streaming tools designed to meet these standards. These platforms reduce risks associated with non-compliance.
Moreover, encrypted live streaming services integrated with AI-powered security features streamline operations. Automated threat detection and protection reduce manual efforts, helping businesses lower operational costs while maintaining secure, efficient workflows.
Business Use Cases with Case Studies
Secure video streaming platforms play a vital role in protecting intellectual property in live video streaming, ensuring businesses can share content safely and effectively. Below are key industries leveraging enterprise-grade video encryption for businesses:
Healthcare
A leading hospital utilizes a secure live streaming platform with DRM to broadcast live surgeries to medical students while maintaining strict HIPAA compliance. This setup demonstrates how to protect business video content from piracy while safeguarding sensitive information.
Corporate Training
Global corporations use affordable secure video hosting solutions for small businesses and large-scale operations alike. Encrypted live training sessions allow remote employees to access sensitive materials securely, adhering to best practices for secure corporate video streaming.
OTT Services
Premium platforms like Netflix rely on DRM to protect their content. This ensures only authorized users can access the videos, helping to address concerns about protecting intellectual property in live video streaming.
By understanding these cases, businesses can choose secure live streaming platforms tailored to their needs.
New Metrics to Evaluate Secure Platforms
When evaluating secure live streaming platforms with DRM, it’s essential to focus on metrics that go beyond the basics. Start with latency, as low latency ensures smooth streams while supporting advanced security features like end-to-end encryption for business video streams. Platforms with high latency may compromise both user experience and the effectiveness of security protocols.
Consider the frequency of security audits. A platform that regularly assesses its systems is more likely to stay ahead of vulnerabilities, especially critical for secure video streaming for financial institutions.
Uptime and resilience are equally crucial. Look for platforms that guarantee high uptime and have proven defenses against Distributed Denial-of-Service (DDoS) attacks. This ensures reliability and protects sensitive content.
By measuring these metrics, you can choose a platform that prioritizes both seamless performance and robust security for your business needs.
Incorporate AI and Automation for 2024-2025 Trends
Adopting AI and automation is redefining secure video streaming, especially for enterprises aiming to comply with privacy laws and enhance content protection. One key trend is AI-powered video content protection through AI-driven watermarking and forensic tools. These platforms embed invisible, dynamic watermarks into video streams, enabling tracking of unauthorized redistribution. With machine learning for secure video streaming, these tools detect and analyze leaks, ensuring robust content security.
Access control is another area of rapid innovation. Biometric and Multi-Factor Authentication (MFA) combines traditional passwords with biometrics, such as fingerprints or facial recognition. This layered security strengthens user authentication while helping platforms adhere to compliance requirements. Enhanced authentication methods not only protect against unauthorized access but also build trust with users.
Additionally, edge computing for secure video delivery is gaining traction. By processing data closer to the user, edge computing reduces latency and improves streaming quality while minimizing risks of data breaches. This approach aligns with privacy laws by keeping sensitive information localized, ensuring a balance between performance and security.
By integrating AI-enhanced DRM for enterprise video, companies can safeguard their content and meet legal standards, preparing for the evolving landscape of secure video streaming in 2024 and beyond.
Real-World Examples for Business Use Cases
Healthcare
Scenario: A hospital broadcasts a live surgery to medical students across the globe.
Solution: Using AES-128 encryption combined with HLS delivery ensures the stream is secure and meets privacy standards.
Outcome: The hospital complies with HIPAA regulations while allowing students worldwide to access valuable educational opportunities.
Platform Example: Platforms like Brightcove and Dacast provide secure streaming with features like DRM and HTTPS delivery. These tools demonstrate how to comply with privacy laws for video streaming effectively.
Corporate Training
Scenario: A multinational company conducts live training sessions for remote employees.
Solution: Dynamic token security ensures only authorized employees can access the sessions. AI-powered anomaly detection helps identify suspicious logins in real-time, enhancing video security.
Outcome: Sensitive internal processes are safeguarded, and employees can securely access training sessions via multi-factor authentication.
Platform Example: IBM Video Streaming offers enterprise-grade security with AI monitoring, illustrating how using AI to detect piracy in video streams enhances protection.
OTT Services (Streaming Services)
Scenario: An OTT platform offers exclusive content for a monthly subscription.
Solution: Blockchain-based DRM secures digital rights, while forensic watermarking identifies and tracks piracy attempts.
Outcome: The platform reduces revenue loss from piracy and builds user trust by offering robust security measures.
Platform Example: Vimeo OTT provides secure paywalls and advanced DRM, showcasing real-time video security with AI monitoring.
Educational Institutions
Scenario: A university provides online courses with premium video content.
Solution: Georestriction limits access to students in specific regions, while DRM prevents unauthorized downloads and sharing.
Outcome: Intellectual property is protected, ensuring compliance with legal requirements while maintaining accessibility for enrolled students.
Platform Example: Panopto supports educational institutions by combining secure streaming with features like georestriction and DRM.
These examples highlight how secure video streaming solutions can meet industry-specific needs while adhering to privacy laws and leveraging AI for enhanced protection.
Emerging AI and Automation Trends
AI-Driven Threat Detection
AI-powered threat detection is becoming a crucial tool for securing online platforms. One specific use case is AI monitoring user activity during a live stream. For instance, it can track login patterns and spot unusual behavior like multiple simultaneous logins from different geographic locations. Behavioral analytics for secure video platforms helps in identifying anomalies in real time, allowing the system to automatically block unauthorized users. This technology reduces the risk of breaches and ensures that content remains protected without needing manual intervention.
Biometric and MFA Integration
In an era where security is paramount, biometric authentication and multi-factor authentication (MFA) are taking center stage. For example, a platform may require users to verify their identity through face or fingerprint recognition in addition to a password. This extra layer of security ensures only authorized individuals can access sensitive accounts. The combination of biometric authentication and MFA is especially beneficial for industries that handle confidential data, like finance or healthcare, where unauthorized access could have serious consequences. It helps to provide a higher level of protection against cyber threats.
Forensic Watermarking
Forensic watermarking is another emerging trend where AI plays a pivotal role in protecting video content. This technology involves embedding invisible watermarks unique to each user. If content is leaked online, these watermarks help trace the source of the breach. AI watermarking technology for video protection is becoming more widely adopted, particularly by industries like Hollywood studios and music producers who need to safeguard pre-release content. By using these watermarks, companies can not only protect their intellectual property but also deter piracy and illegal distribution.
These trends in AI and automation are revolutionizing how we secure digital content, offering robust solutions that make online platforms safer for both creators and users.
Blockchain Technology for Digital Rights Management (DRM)
How It Works:
Blockchain technology uses a decentralized ledger to record licensing and distribution rights, ensuring data transparency and tamper-proof security. Each transaction, such as a video purchase, is added as a block to the chain, creating an unalterable record. AI-driven dynamic tokenization for video security further strengthens this process by assigning unique digital tokens to each piece of content.
Benefits:
Blockchain helps prevent unauthorized duplication and distribution of content. It also simplifies royalty tracking, ensuring content creators are properly compensated. By combining Blockchain and AI for video streaming security, platforms can offer enhanced protection against piracy.
Example:
Streaming platforms like Eluvio are leading the way in integrating blockchain with AI in secure video broadcasting for businesses, providing a robust solution for video content delivery.
New Metrics for Evaluating Secure Platforms
When evaluating secure video streaming platforms, consider these key metrics to ensure both performance and protection:
- Encryption Type: Look for AES-128 or higher to secure data.
- Latency: Aim for less than 3 seconds for live streams to maintain smooth delivery.
- Compliance Standards: Ensure adherence to regulations like GDPR, HIPAA, or PIPL.
- Multi-Factor Authentication: At least two factors, with biometric options preferred.
- AI Monitoring Frequency: Opt for real-time or checks every 5-15 minutes for constant threat detection.
- Blockchain DRM: Ideal for protecting digital rights and preventing piracy, especially with sensitive content.
- Scalability: Choose platforms that can scale securely without compromising data protection.
These factors help users choose a secure and reliable video streaming platform.
How AES Encryption Works
AES (Advanced Encryption Standard) is a symmetric encryption algorithm used to secure video data. In AES-128, data is encrypted with a 128-bit key, broken into blocks and transformed through multiple rounds of substitution and permutation. Each round ensures the encrypted data becomes increasingly difficult to decrypt without the correct key.
Dynamic tokenization adds another layer of security by replacing sensitive data with a token. These tokens are checked and refreshed every two minutes to prevent unauthorized access.
The evolution of secure streaming has progressed from basic password protection to advanced technologies like blockchain and AI, ensuring safer and more efficient content delivery.
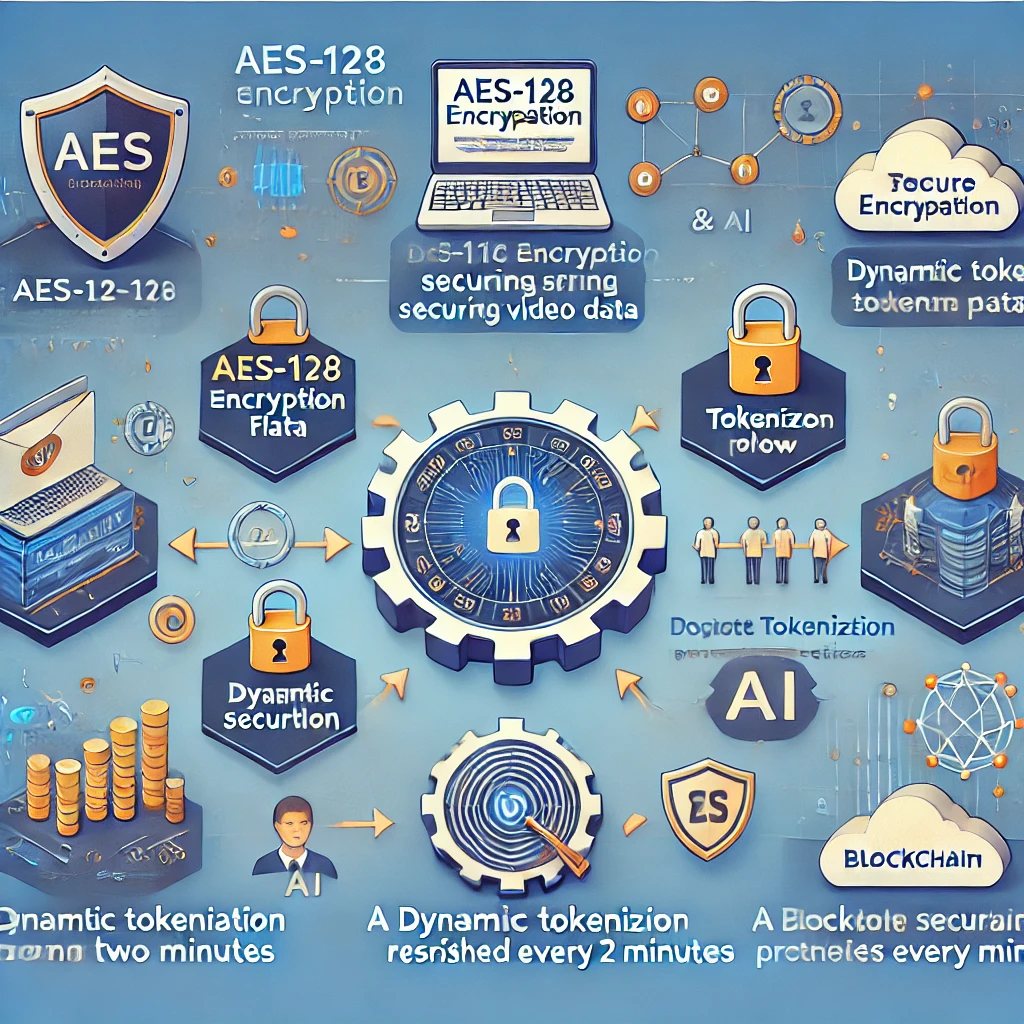

The above infographic illustrates AES-128 encryption, dynamic tokenization flow, and the evolution of secure streaming technologies. It shows the encryption process, token security checks, and a timeline of key advancements in secure streaming.
Top 7 Features for Secure Video Delivery
There are specific features that are designed to support secure video streaming. These security options are available for hosting secure live streams and on-demand video libraries.
Let’s take a look at some of the top features to look for when you’re comparing video hosting platforms for secure streaming.
1. Password Protection

One of the most basic forms of security for your videos is password protection. This option enables you to set a password blocking your video content before anyone can view it. As long as you can ensure the privacy of your password, your stream will be secure.
This method can be essential for use within a small business or organization, or to pass around a video privately before publicly sharing.
If you are thinking of using password-protected streaming, please keep in mind that this method is not bulletproof. It is easy for passwords to be leaked among friends and colleagues or even in online forums.
In order to keep things secure, change your video passwords every couple of months and do routine checks on Google for leaked passwords. Simply search “password for [VIDEO NAME] + [YOUR BRAND], and any forums that have your leaked password should pop up.
2. Geographic and Domain Restrictions
There are two types of viewer restrictions that broadcasters can use to protect online video.
The first is a domain restriction. As the name implies, this setting restricts the domains on which your stream is playable. When setting up this feature, you type in the websites on which you’ll allow your videos to play.
Once up and running, embedding your video on any other website will fail. This helps to prevent others from embedding your video player on their website, which helps to avoid pirating.
The second type of restriction is geographic restriction. This method uses IP addresses to whitelist certain countries. Similar to the above method, you select which countries can view your videos. Users living outside these countries will not be able to watch.
Geo-restrictions are great if you are serving an audience within very specific locations.
This method is highly accurate and provides an additional layer of security.
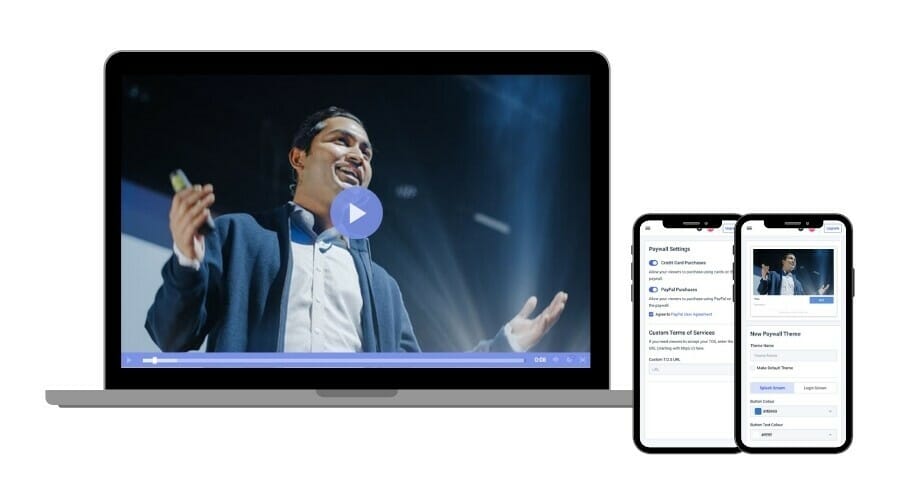
3. Secure Paywalls

If you are monetizing your online videos and live streams, payment security is critical. Without strong payment security measures, you may lose many customers due to mixed-content warnings. In the worst-case scenario, you could get bad press or even legal action for failing to protect customer information.
Dacast uses an in-player payment system. This method is fully HTTPS and uses bank-grade SSL encryption to protect payment information again malicious actors.
Dacast also prevents the sharing of login information to bypass the video paywall. Users who have purchased access to videos or live video streams are only authorized to be logged in on one device at a time. When another login is detected via another device, the original stream will shut down.
4. Dynamic Token Security System
One advanced method that is used to ensure video security is tokenized video delivery. This security feature is especially valuable for video content that you embed in any site or app.
With a dynamic tokenized security system, the video player calls the server for a new token every two minutes. This ensures that domain restrictions, geographic restrictions, and other security measures are constantly checked and cross-checked. If the wrong tokens or no tokens are present, the video playback will immediately fail.
This process is completely transparent to the user, yet it provides a hard-to-bypass additional layer of security for your content.
5. System Monitoring
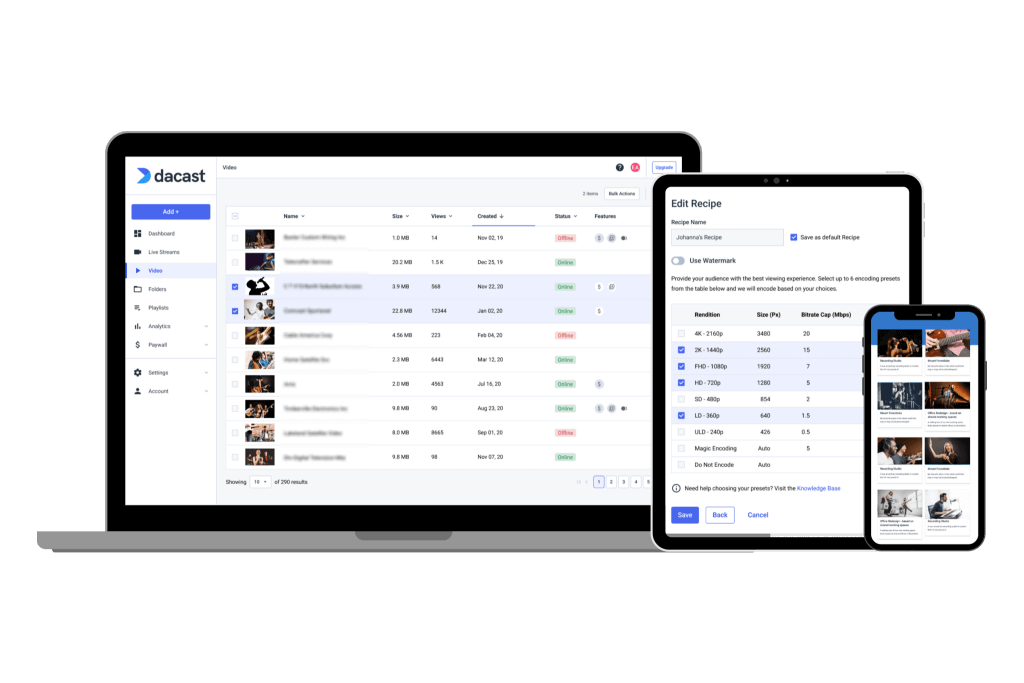

Choose an online video platform that has system monitoring. This will help to identify any red flags or indications of security threats.
The Dacast streaming solution is monitored by both automated and human-managed security scans, tests, and checks. For example, video content storage requires SSH public-key authentication. Security managers review the integrity and access to this system daily.
6. HLS Video Encryption
HLS stands for HTTP live streaming. While there are many types of encryption algorithms, the most commonly used method for HLS encryption is AES-128. Advanced Encryption Standard (AES) is a block cypher that encrypts and decrypts data in 128-bit blocks. Here are the basics of how AES-128 works.
In video streaming, broadcasters can add AES video encryption that can be to a stream for security purposes. When the video is encrypted, a special key scrambles the video content. Unless the viewer has the correct access key, they can’t watch the video. Furthermore, if they try to intercept it, all they’ll see is a scrambled mess of useless data.
At the same time, authorized viewers have access to AES-encrypted video via their web browser and a secure HTTPS connection. The encryption process is invisible but provides a significant layer of protection against interception and piracy.
7. HTTPS Video Delivery
HTTPS is an encrypted web communication standard often used by government organizations, banks, and other industries with data that needs to be kept private. This protocol provides security in three ways.
First, it prevents tampering when the video file is in transit. Encrypted data cannot be changed while moving through the internet without destroying the data completely.
Second, HTTPS provides authentication. You can usually be sure that data sent via HTTPS connections truly came from where you think it did.
Finally, in conjunction with HLS delivery, HTTPS protects from eavesdropping. Implemented correctly, no one but the intended recipient should be able to access the data being transmitted.
Popular Use Cases for Secure Streaming



 Connect
Connect
 Events
Events Business
Business Organizations
Organizations Entertainment and Media
Entertainment and Media API
API Tools
Tools Learning Center
Learning Center Support
Support Support Articles
Support Articles